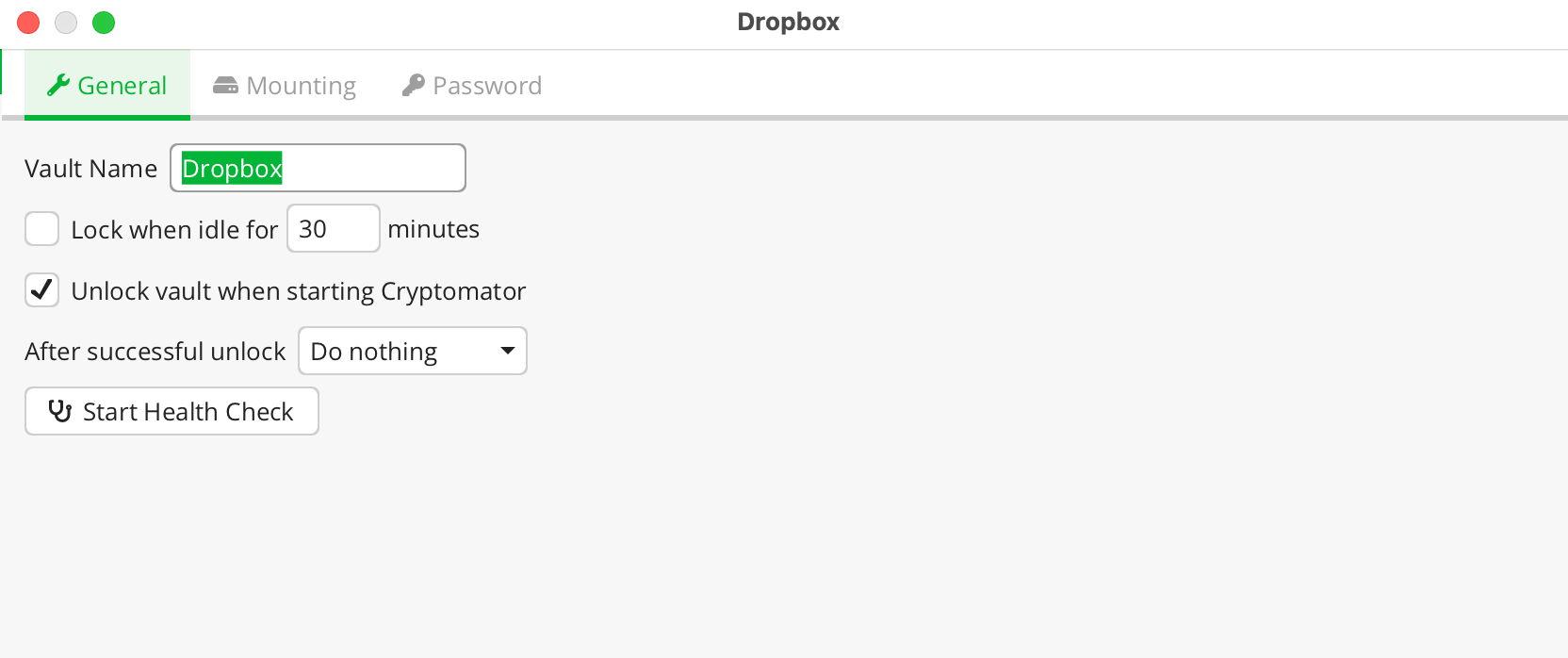
Cloud storage is incredibly convenient and much cheaper than running your own servers especially if you don't have that much to backup and most open source self hosted backup solutions are not so great in comparison.
They don't generally have encryption at rest or on device and the ones that do offer this feature have bandwidth problems, lack basic features, or are riddled with false claims and vulnerabilities. Have these companies given us any reason to trust them? on the contrary they have given us many reasons to not.
Below are just a few examples of Cloud providers failing to secure your private data.
Cloud Provider Privacy & Security Incidents
1. MEGA - previously known as (MegaUploads)
2022 Vulnerability Discovery: Security researchers from ETH Zurich published findings detailing significant vulnerabilities in MEGA's cryptographic implementation. They demonstrated methods that could potentially allow MEGA (or someone controlling their servers) to recover user RSA private keys over time and decrypt user data, or insert malicious files undetected.This highlighted that MEGA's E2EE implementation had critical flaws undermining the "zero-knowledge" promise under certain attack scenarios. MEGA acknowledged the research and implemented mitigations.
- Cloudwards - MEGA Security Flaw Review
- The Hacker News (References 2022 research)
- History Behind MEGA and MegaUploads
2. Google Drive
Shared Link Vulnerabilities: Historical issues and design choices sometimes allowed links to be accessed more broadly than intended. Google implemented a security update in 2021 to make links more secure.
Misconfiguration Risk: Improperly configured sharing settings by users/organizations have led to data exposure (e.g., the reported US DoD incident).
Associated with the NSA program (PRISM): This is an NSA program to work with internet providers and tech companies to harvest data.
3. Dropbox
2011 Authentication Bug: A critical bug allowed access to any Dropbox account using any password for approximately four hours.
2012 Password Leak (2012 Breach, Disclosed 2016): A breach resulted in the theft of email addresses and hashed/salted passwords for tens of millions of users.
4. Multiple E2EE Providers (Sync.com, pCloud, Tresorit, Seafile, etc.)
Issue (Implementation Vulnerabilities - per Oct 2024 Research): Research from ETH Zurich found various cryptographic vulnerabilities across several E2EE cloud storage providers. Issues included lack of user key authentication, potential for downgrade attacks, and link-sharing pitfalls. This demonstrates that securely implementing E2EE is complex, and vulnerabilities can exist even in privacy-focused services, requiring ongoing scrutiny.
The logical next question is how can we take advantage of the reliability, availability and ease of use while maintaining our privacy and security?
In this article I will show you the most comprehensive and convenient way to encrypt and utilize any cloud storage provider using Cryptomator, I will be demonstrating this with Dropbox but this will work for any cloud provider since the only data being sent to the cloud provider is encrypted.
What is Cryptomator?
Cryptomator is an of open-source software designed for the purpose of encrypting your cloud files easily and mounting them as if it were part of your file system naturally.
Platform Availability:
Desktop Setup Cryptomator with Dropbox
- Install Cryptomator.
- Press the plus sign on the bottom left → Create New Vault → Select the Dropbox folder.
- Give it a strong password preferably generated from your password manager.
- Cryptomator creates a specific folder structure and adds configuration files within the dropbox folder. Dropbox will start synchronizing these files.
- When you want to access your secure files, you open Cryptomator, select your vault, unlock and enter your password.
- You can choose to have Cryptomator to
[x] Remember Password.
This what I choose to do since my system is encrypted and it requires a password to get into my computer the purpose of this system is to prevent Dropbox from accessing our files nothing else. This is also what will enable you to have a seamless experience which is why we are doing this in the first place.
[x] Rember my choice, don't ask again → Done - Cryptomator mounts a new virtual drive on your computer, you can designate this mount location, by default it has a couple different mount locations depending on the volume type.
- Now you can add any files you want to be synchronized to the virtual drive that you designated, mine is
/Users/[USERNAME]/Documents.
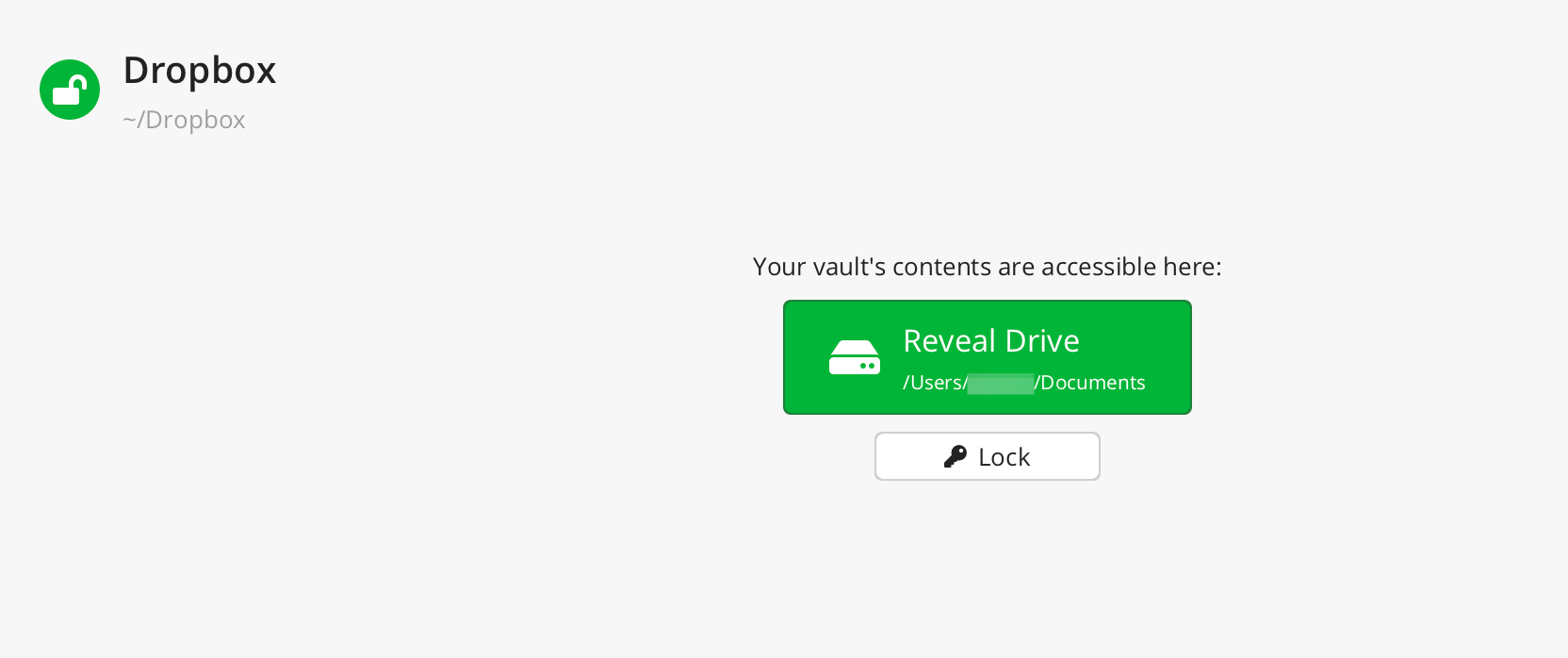
Important Vault Mount Options
[VAULT_NAME] → Vault Options → Mounting
-
MacFUSE (MacOS)
You should install macFUSE for macos, this requires enabling kernel extensions which does lower your security but macFUSE is much better than the other option fuse-t, but you can use that one if you would like. -
FUSE (Linux)
This would be similar to MacFUSE and would be my recommended volume type for Linux -
WinFS (Windows)
This would be similar to MacFUSE and would be my recommended volume type for Windows. -
WebDAV
This option does work but I wouldn't recommend it as it runs as a server on your computer and adds additional overhead causing a performance hit. This also does not allow for execution
These mount flags are neccessary to allow for writing and executing files within the mounted virtual drive.
-
MacOS Mount Flags
-orw,exec,uid=501,gid=20 -
Linux Mount Flags
-orw,exec,uid=$(id -u),gid=$(id -g)
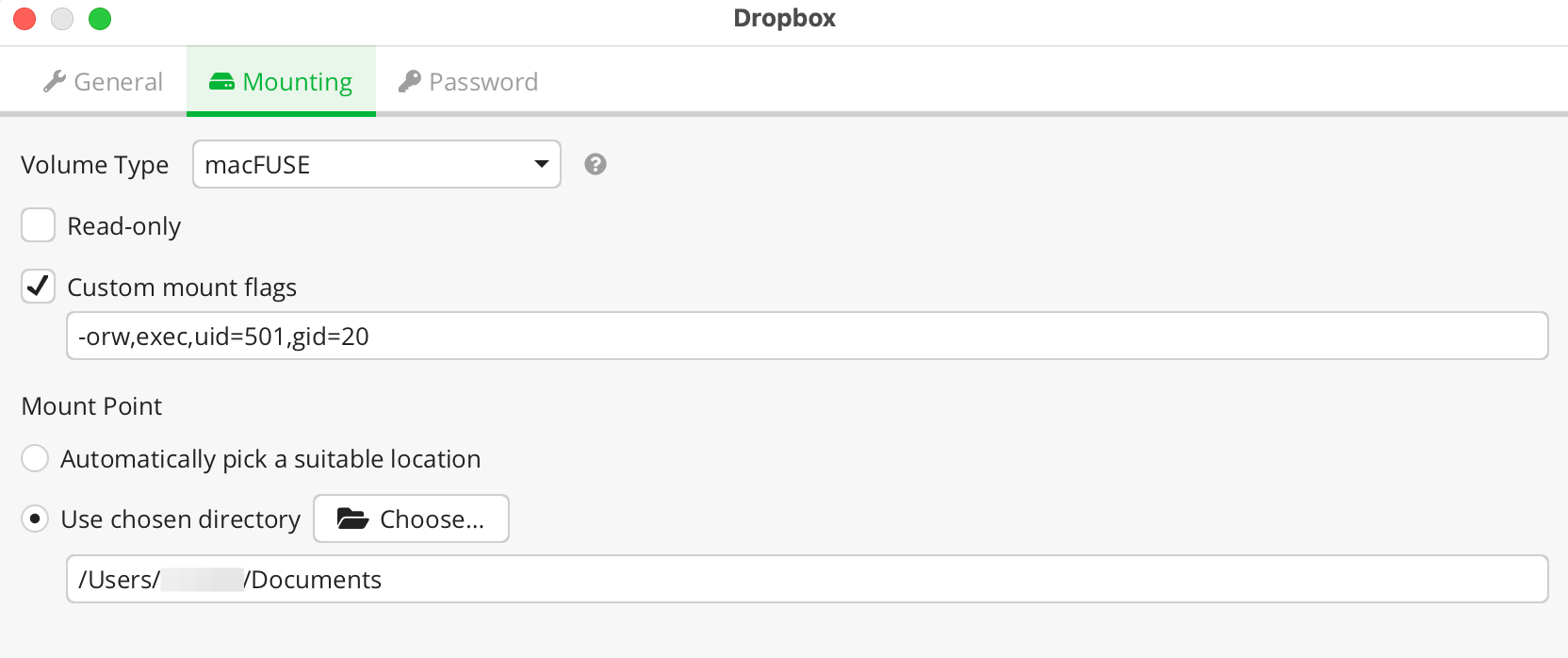
Auto Mount Configuration
This configuration will set your vault to unlock when the device is started, allowing for a seamless setup.
- MacOS:
~/Library/Application Support/Cryptomator/settings.json- Linux:
~/.config/Cryptomator/settings.json- Window:
%APPDATA%\Roaming\Cryptomator\settings.jsonand change the unlockAfterStartup value:
"unlockAfterStartup": true → "unlockAfterStartup": false.Settings → Preferences → General
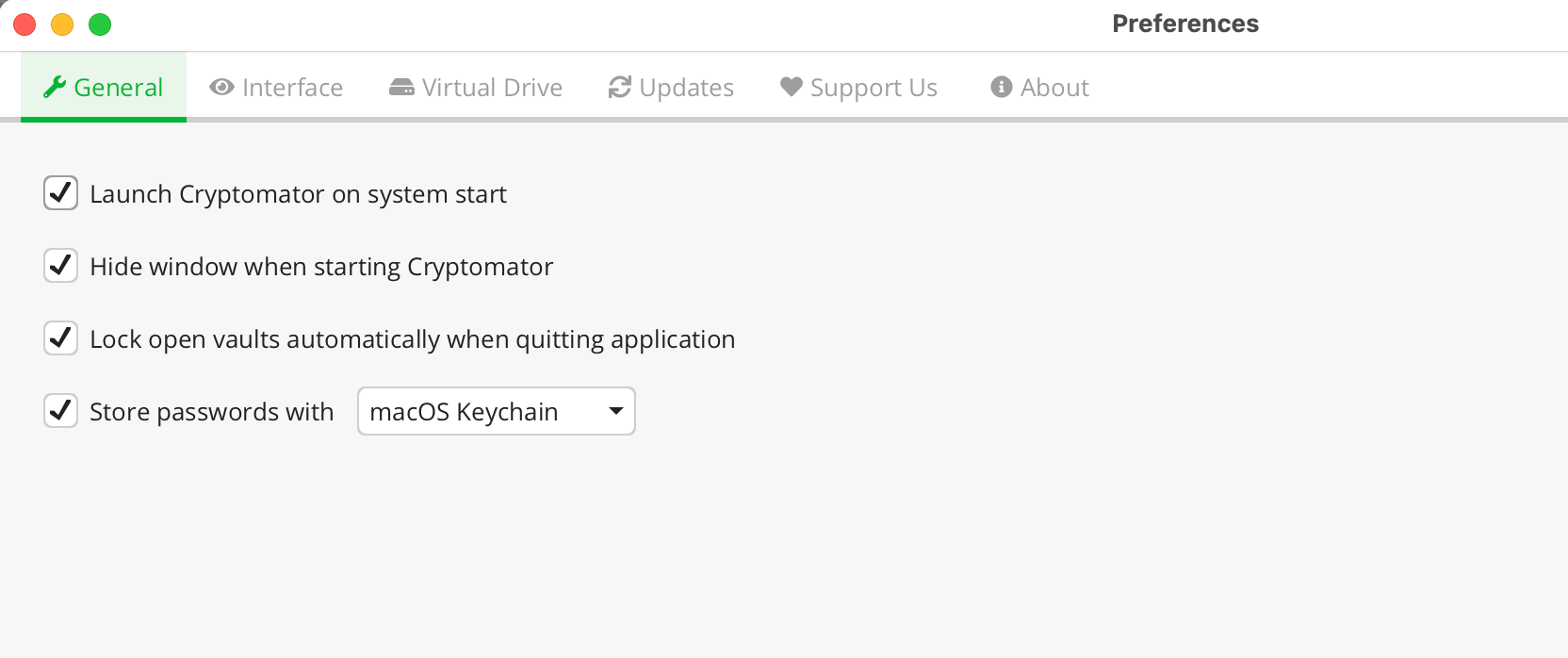
[VAULT_NAME] → Vault Options → General